With the release of FortiOS 7, Fortinet added a new feature that supports Automated Certificate Management Environment (ACME) as defined in RFC8555.
This allows administrators to use the free SSL certificates, provided from Let’s Encrypt.
Note:
Certificates issued by Let’s Encrypt are free of charge, but are only valid for 90 days.
Unlike most other certification authorities, Let’s Encrypt supports a fully automated process to request, renew and revoke certificates at any time, without any user interaction after the initial setup. All you need to have, is a small agent on the webserver where you want to use the certificate. This agent communicates with Let’s Encrypt to request (and renew) the certificate. In addition, the agent running on the server must be reachable via the internet using the DNS name, the certificate was (or will be) issued to.
So, with FortiOS 7, we can use this type of certificates on our firewalls. Great, isn’t it? No need to purchase certificates for SSL-VPN or publishing internal webservers, anymore.
But (there is always a but in IT, isn’t it?) When enabling SSL-VPN on the WAN interface of a FortiGate firewall, retrieving SSL certificates from Let’s Encrypt seems to be impossible at afirst glance, because Let’s Encrypt requires to reach the ACME agent on the firewall for verification and update requests.
The default setting on the FortiGate however, forwards all traffic arriving on the interface’s IP to the VPN login page, so the ACME agent cannot be reached.
Note:
I know, there are other challenge types to request a certificate from Let’s Encrypt, like DNS-01. But in this case, I needed a way to use the default HTTP-01 challenge.
When talking to the Fortinet tech support about this issue, they recommended changing the port for SSL-VPN from TCP/443 to something else. I never liked that idea, since it would prevent opening a VPN tunnel, when being myself behind a firewall, I don’t manage myself and that blocks non-default ports.
The solution was provided to me by Axel, a good friend of mine and it’s as simple, as brillant:
Axel found out that all you need to do, is disable the button “Redirect HTTP to SSL-VPN” on the SSL-VPN settings page of the FortiGate (VPN -> SSL-VPN Settings):
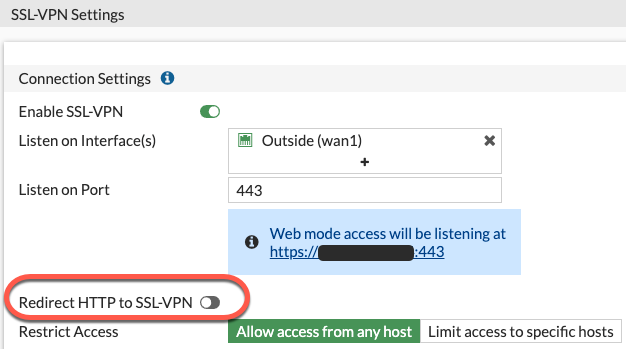
This makes the Let’s Encrypt agent available on TCP/80 while still running the VPN portal on TCP/443. And if Let’s Encrypt cannot reach the ACME agent on TCP/443, they do a fallback test on TCP/80, which works fine, now.
Of course, now your users have to type “https://…” to reach the VPN portal but most users I know, use bookmarks for these addresses anyway or even use the FortiClient to connect to VPN.
So, in case you’re facing the same situation and want to use Let’s Encrypt certificates and SSL-VPN at the same time on your WAN interface, here’s a possible solution for you.
